KMC CONTROLS CSC-2004 Normally Closed, WC, Pneumatic VAV Reset Volume Controller, Reverse ACTUATORING, 1IN: Electronic Components: Amazon.com: Industrial & Scientific
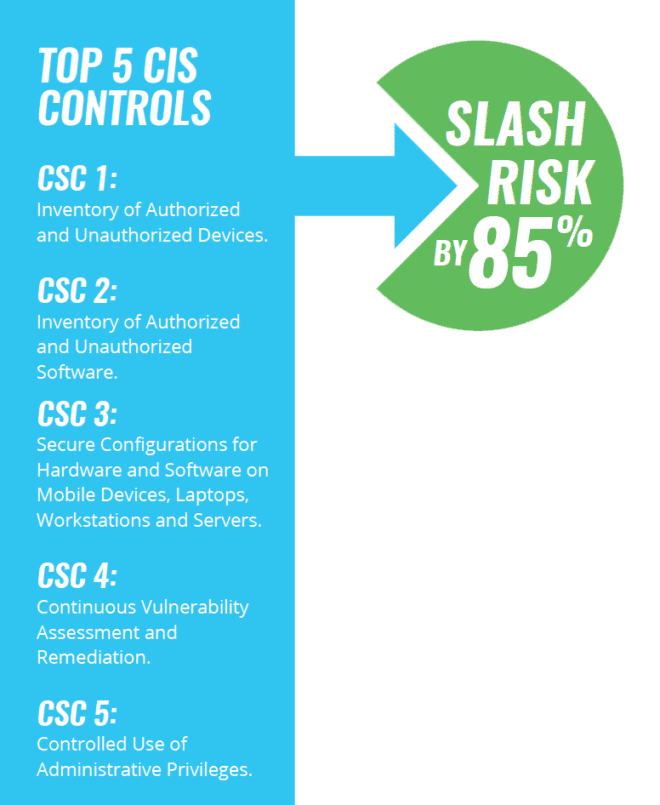
Achieve Continuous Security and Compliance with the CIS Critical Security Controls | Qualys Security Blog

CSC-3011-10 - KMC Controls CSC-3011-10 - Multi-Function Pneumatic VAV Reset Volume Controller - 0-1" Range, 8 PSIG start, "Universal"

CSC-3025-10 - KMC Controls CSC-3025-10 - Multi-Function Pneumatic VAV Reset Volume Controller - 0-2" Range, 8 PSIG start (High Flow), "Universal"

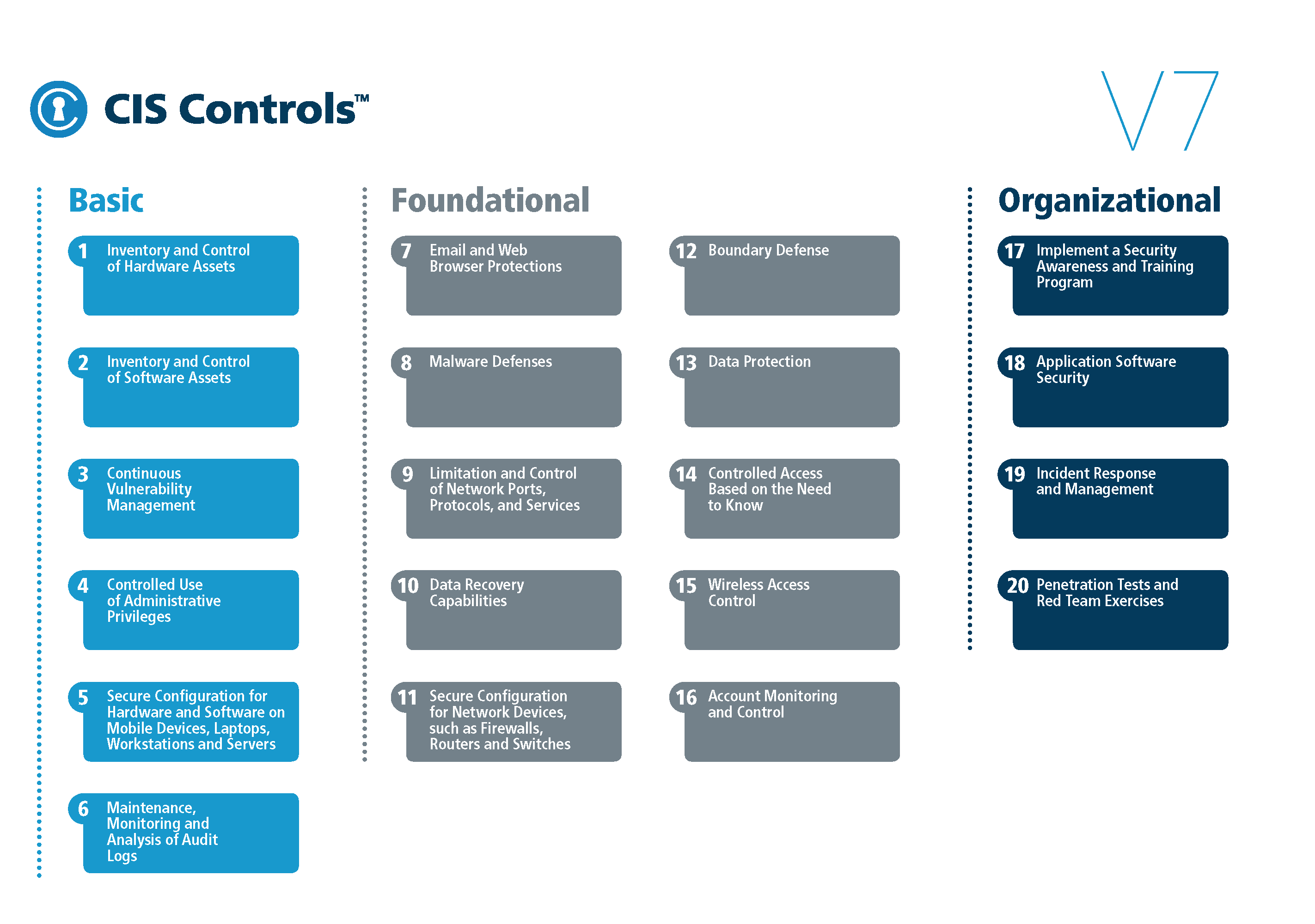
6 CIS CRITICAL SECURITY CONTROLS (CSC) FRAMEWORK SOURCE (KENNEDY, 2017). | Download Scientific Diagram