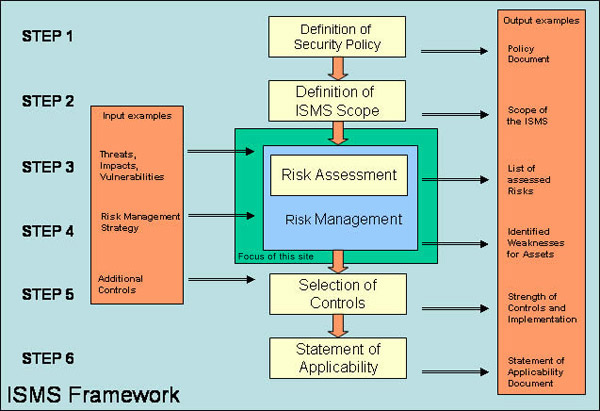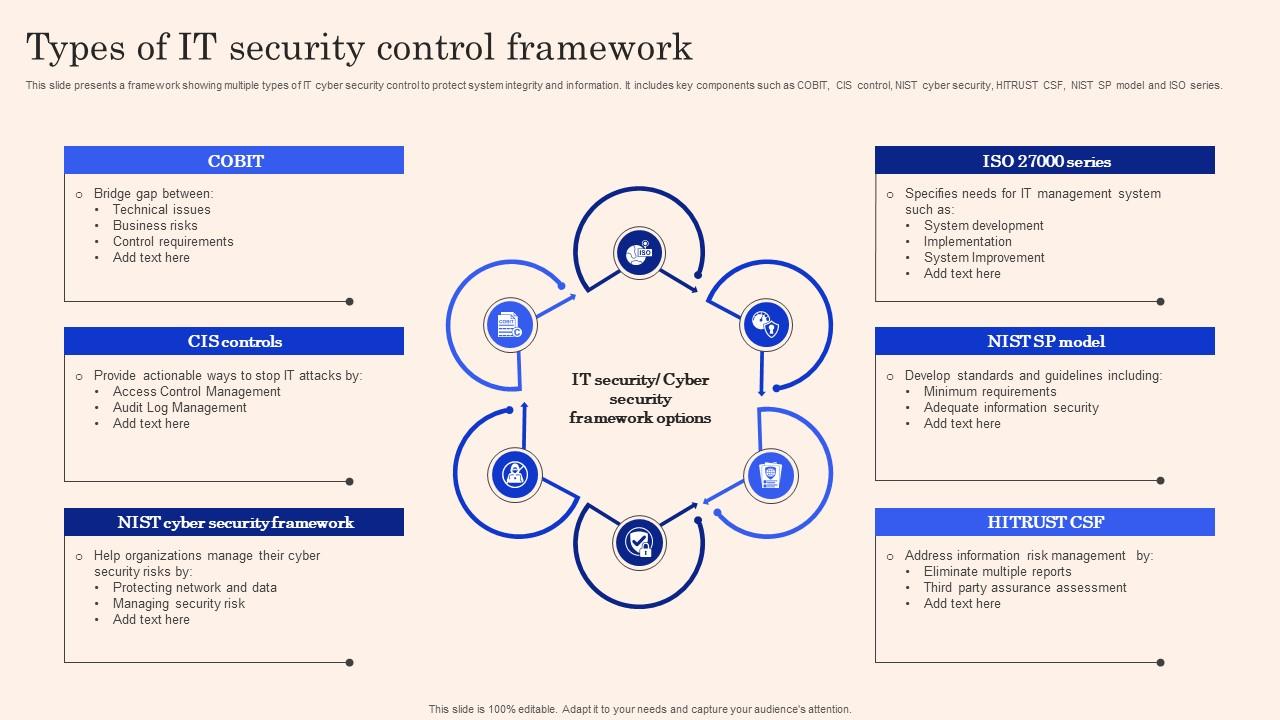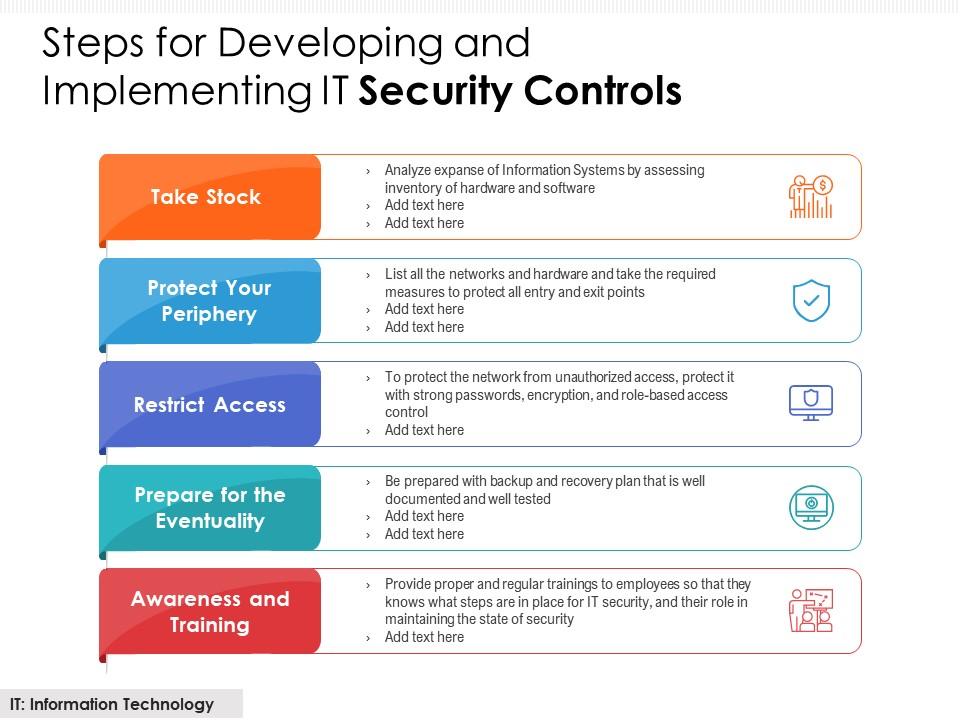
Steps For Developing And Implementing IT Security Controls | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

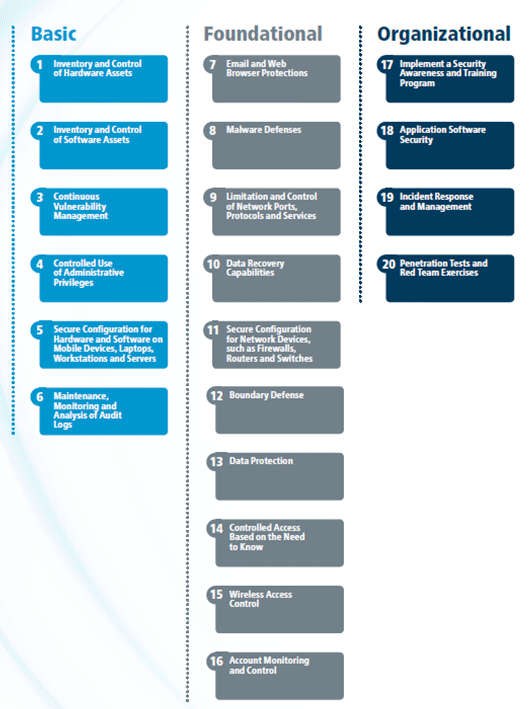
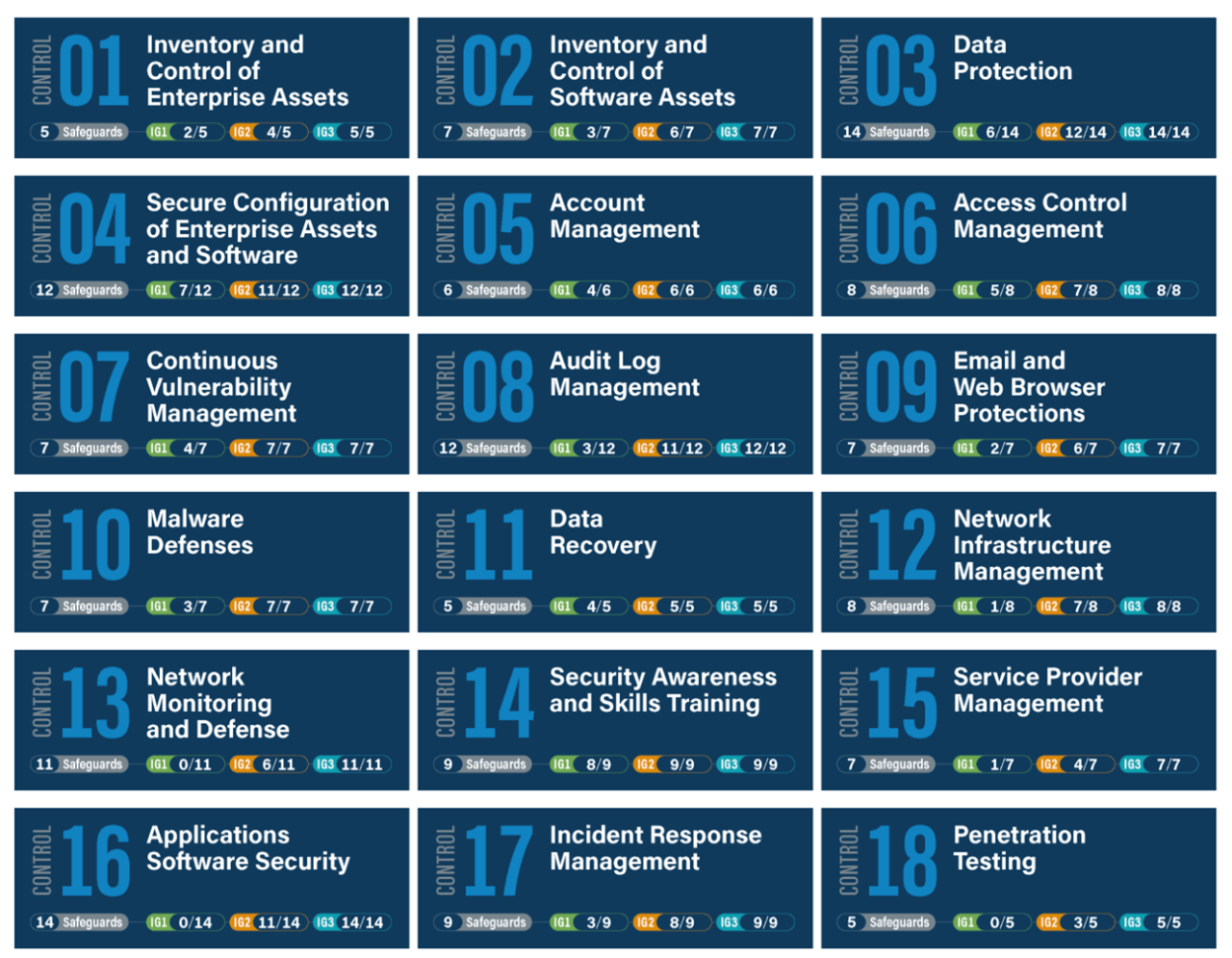
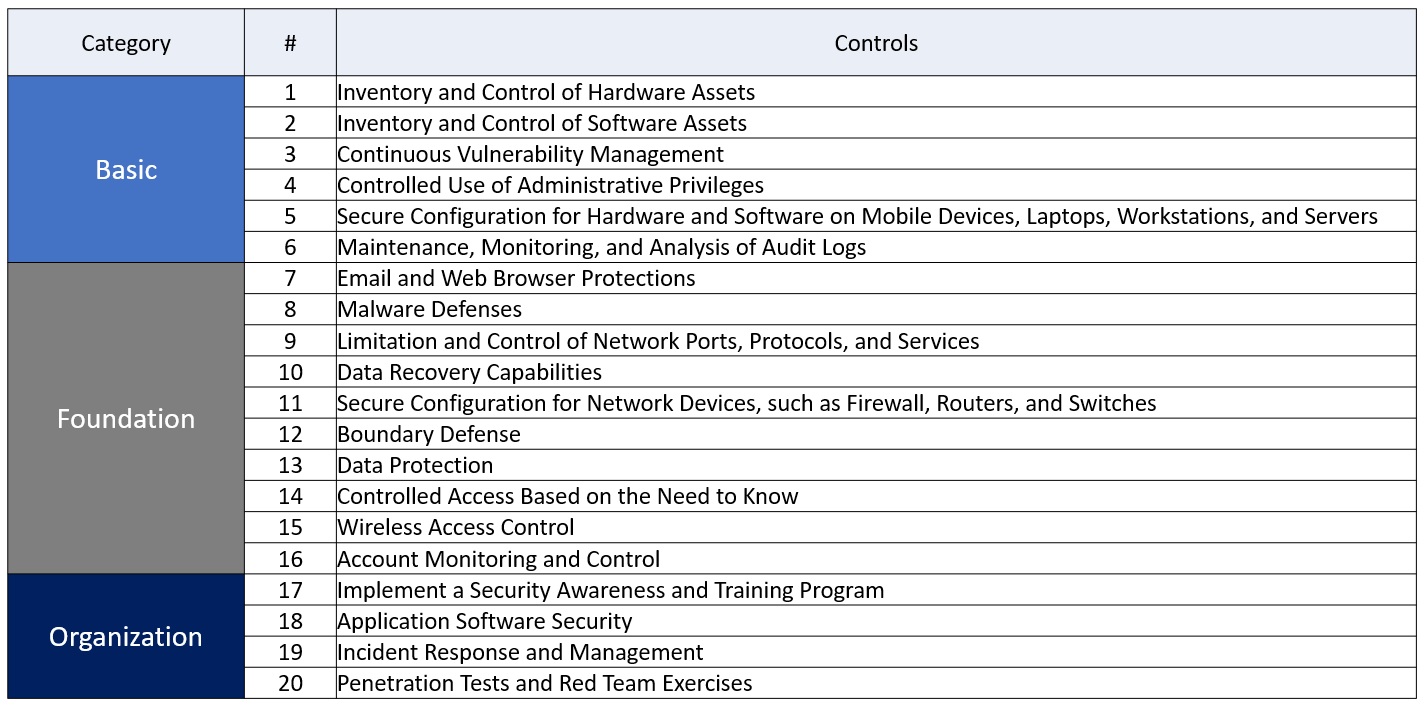
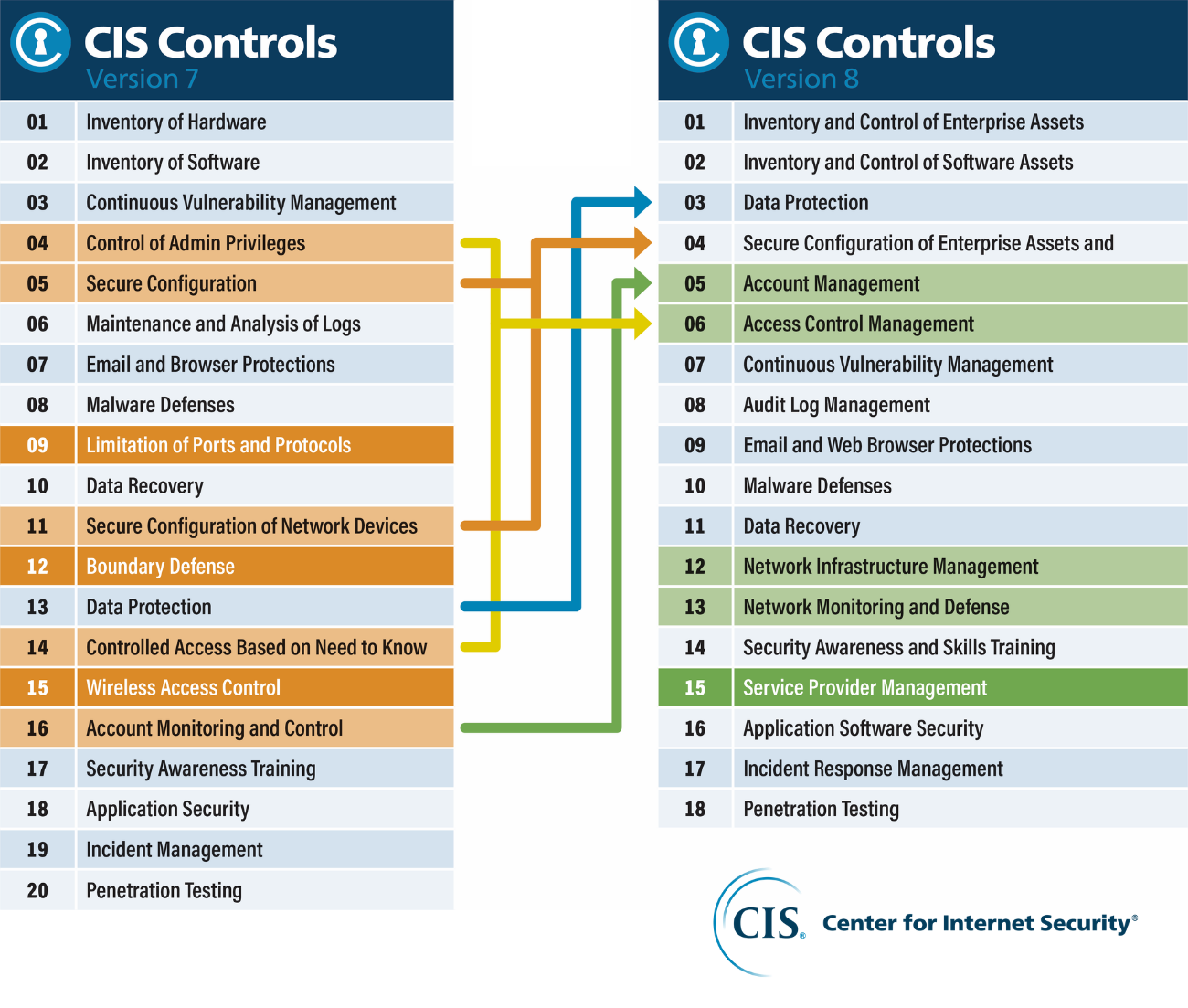
O.L.I.T. Informatica 🌐 on X: "CIS Security Controls (Sans 20) #GDPR # Cybersecurity #DPO #Privacy #ICT #DataProtection https://t.co/mwPrnvxLen https://t.co/GLQArb1BrW" / X

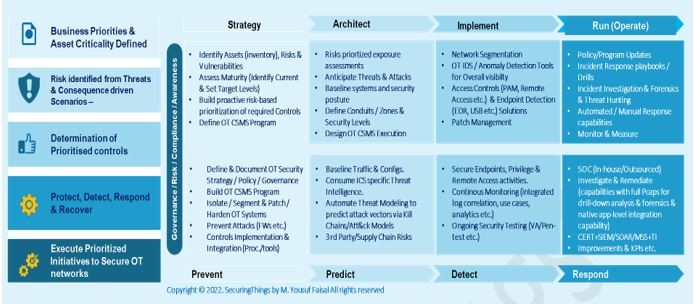
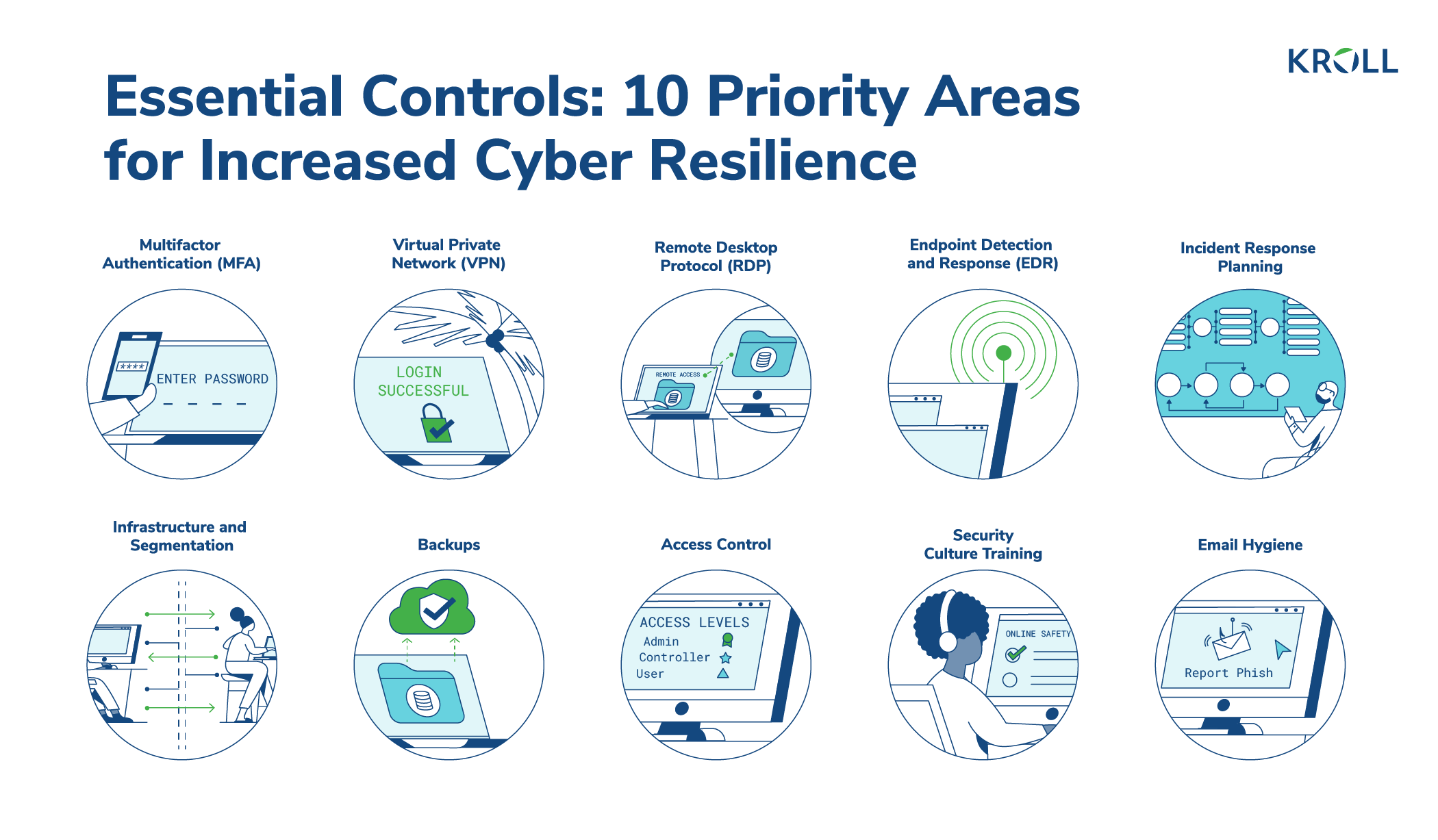
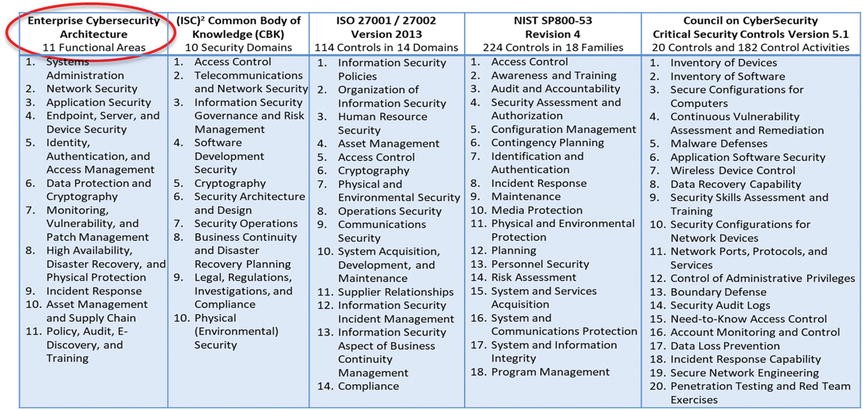
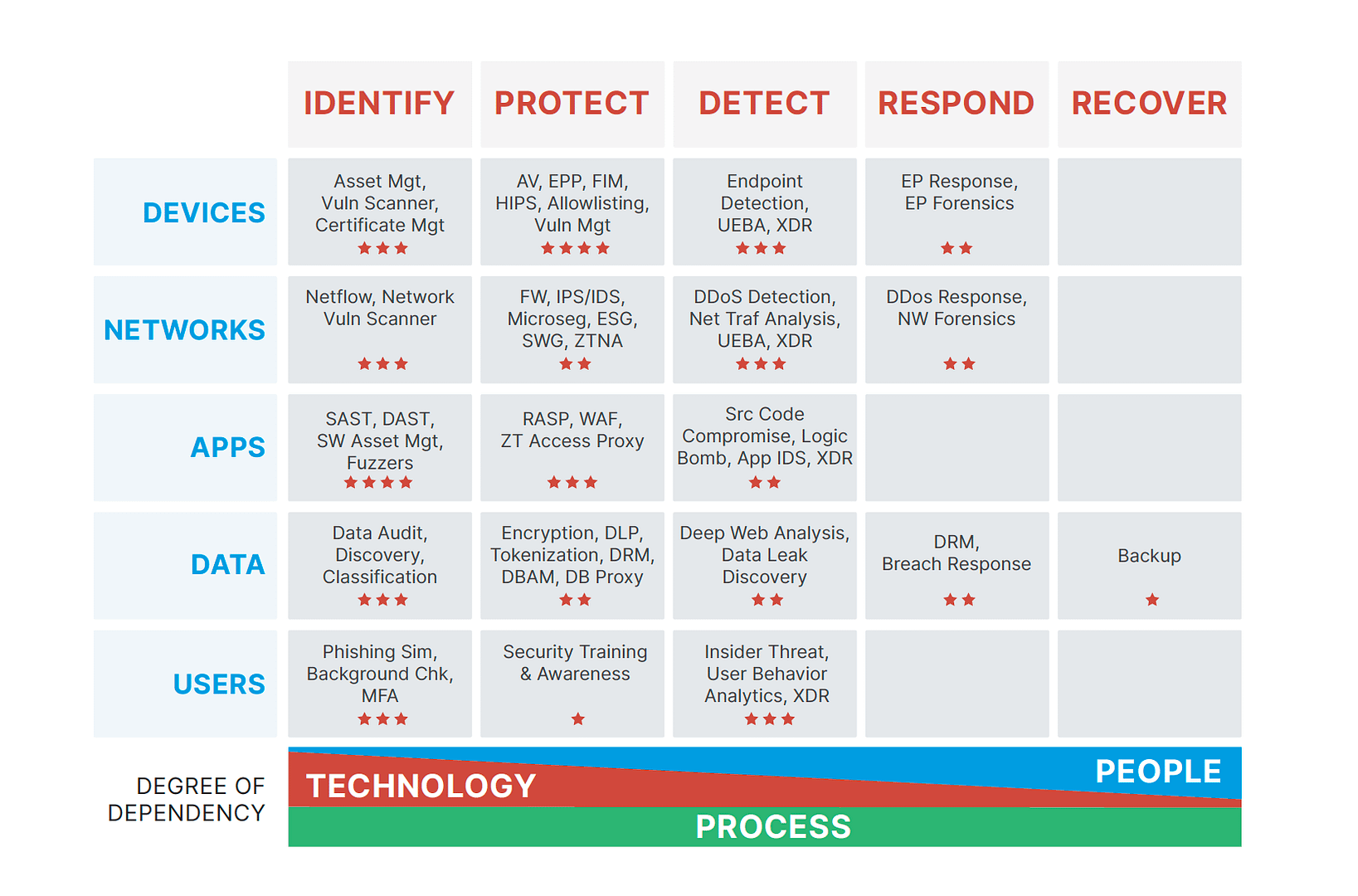
CISO-Level Guide: Protecting Your Organization - Cyber Resilience and Financial Organizations - Carnegie Endowment for International Peace