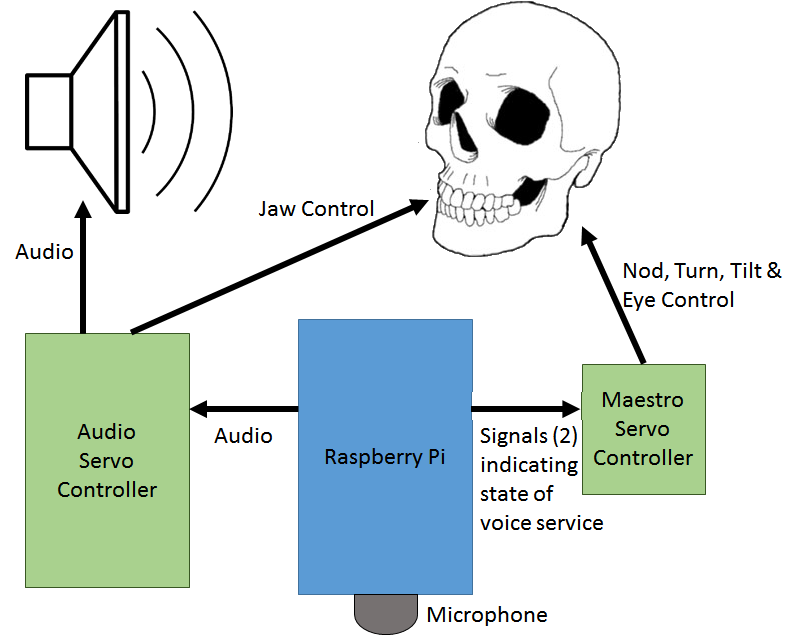
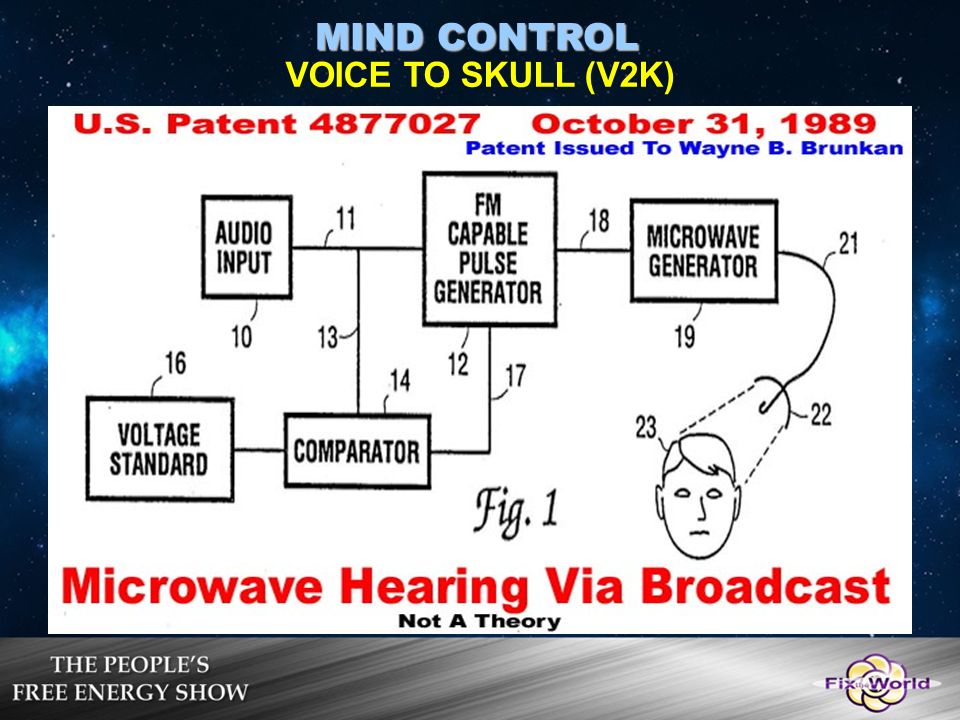
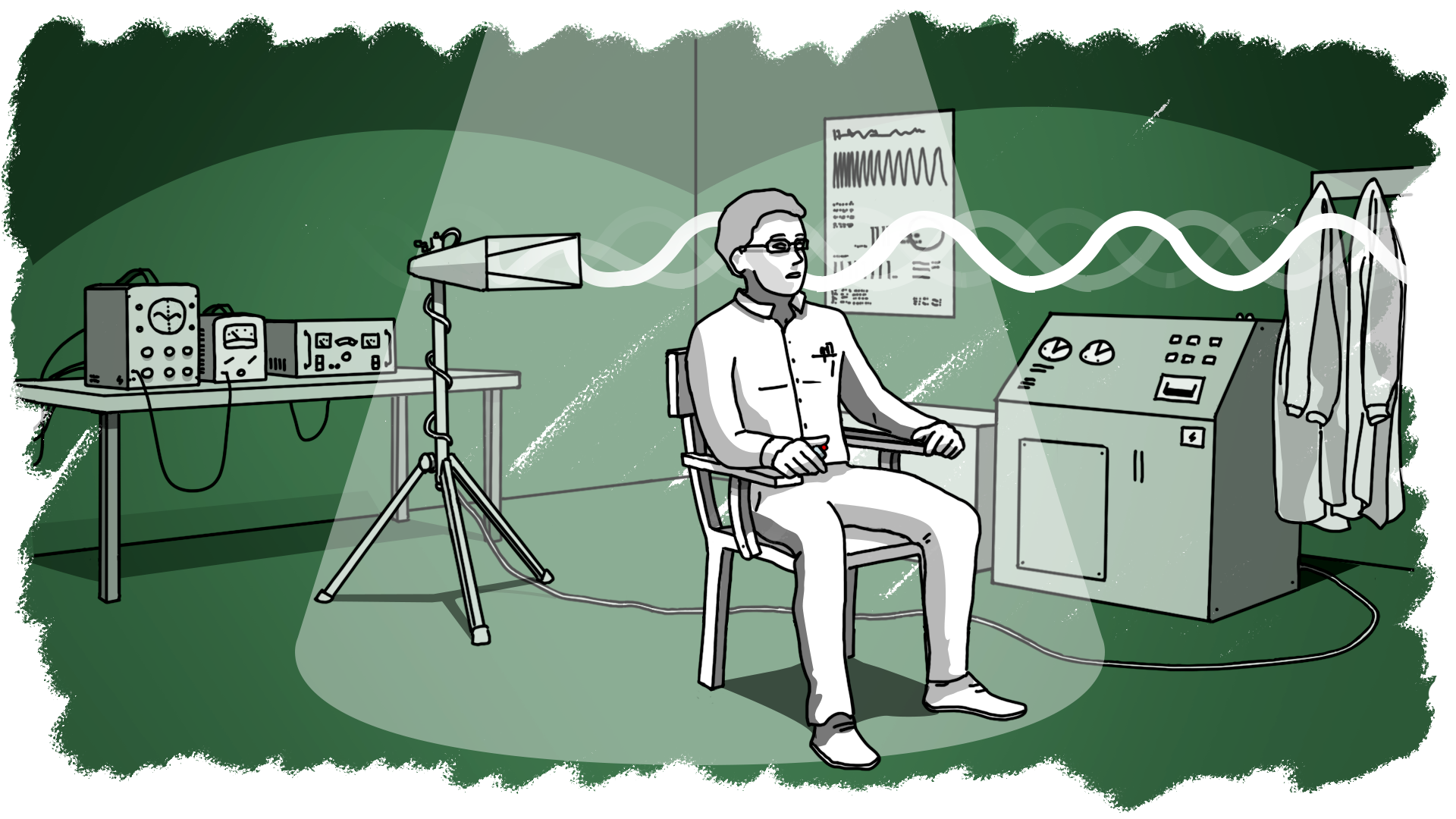
Dawid Gonia on LinkedIn: V2K voice to skull isn't only a sound projected to your mind but also… | 47 comments

Amazon.com: The Radiohead Protocol: At last V2k Mind-Control has an Alpha. And an Omega. eBook : Angel, Electric: Kindle Store

US20200275874A1 - Methods and Automatic System to Identify Who is Victims of Abuse Voice to Skull & Remote Neural Monitoring Technology and Identify Who is Remote Attacker or Operator Using Device of

Eric Griffin on Instagram: "Basic Info > V2K John Lennon on Insanity: “Our society is run by insane people for insane objectives. I think we're being run by maniacs for maniacal

Dawid Gonia on LinkedIn: V2K voice to skull isn't only a sound projected to your mind but also… | 47 comments
V2k Satellite, Voice to Skull technology, often abbreviated as V2K, is a controversial method that purportedly allows individuals to hear sounds, voices, or messages directly ….